Learn AWS by Doing with New AWS Hands-On Training!
Linux Academy
APRIL 19, 2019
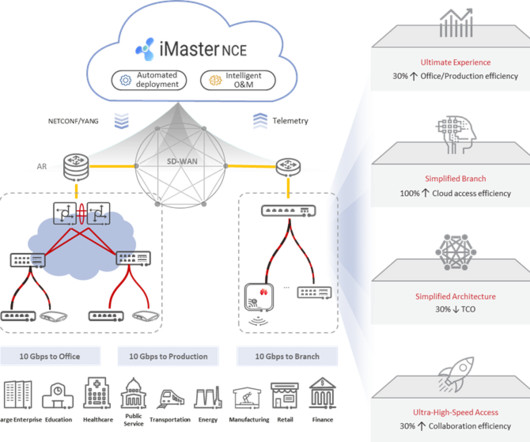
With engaging features like live AWS cloud sandboxes and servers, Interactive Diagrams, Hands-On Labs in live cloud environments, customizable flashcards, study groups, direct access to our expert Training Architects, downloadable Course videos, and more, Linux Academy is the #1 cloud training platform that helps you learn AWS by doing.





























Let's personalize your content