Android Agent Smith mobile malware hits millions of devices
CTOvision
JULY 10, 2019
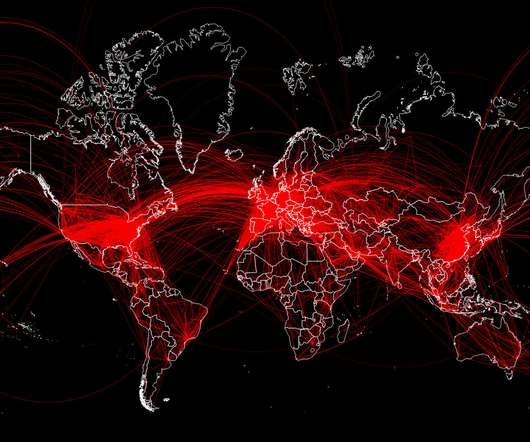
Mobile malware dubbed Agent Smith has infected about 25 million devices, mainly in India and other Asian countries, but other countries have also been affected, including the UK and US, according to security researchers at Check Point Software Technologies.

















































Let's personalize your content