Using X.509 Certs for DID Provenance
Phil Windley
APRIL 25, 2024
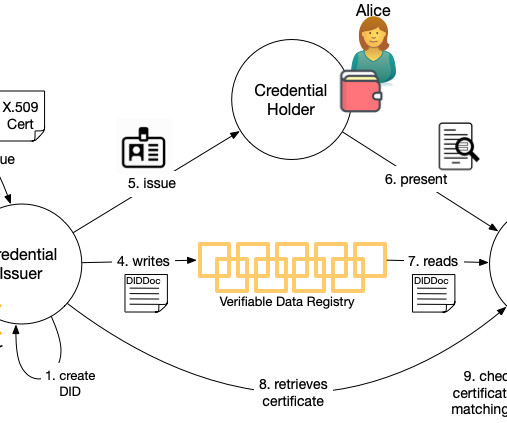
509 certificate authorities who already perform identity proofing for businesses provides a rich resource that can be leveraged to boot the verifiable data ecosystem. For that, they need to take the issuer's decentralized identifier (DID) that they got from credential presentation and determine who it belongs to.










































Let's personalize your content