Securing Your eBook in 2024: Top eBook Protection Strategies
Kitaboo
FEBRUARY 22, 2024
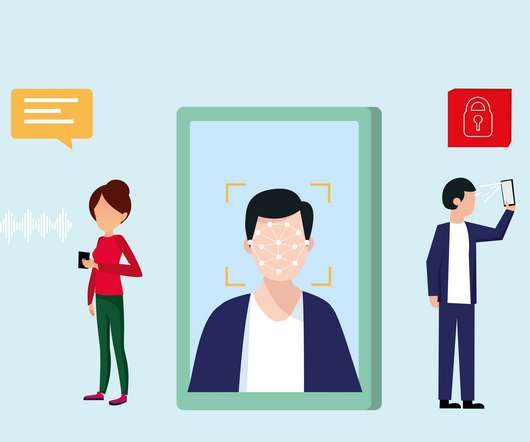
In this blog, we will discuss the various strategies and best practices for securing online books. Types of eBook Protection Strategies to Explore in 2024 Digital Rights Management (DRM) Watermarking Securing eBook Files Secure Distribution Platforms Limit eBook Downloads III. Table of Contents: I.


















































Let's personalize your content