Does Your IT Organization Need an AI Team?
Information Week
AUGUST 22, 2023
Artificial intelligence is rapidly emerging as an essential enterprise tool. Is it time for IT organizations to form their own dedicated AI teams?

Information Week
AUGUST 22, 2023
Artificial intelligence is rapidly emerging as an essential enterprise tool. Is it time for IT organizations to form their own dedicated AI teams?

Social, Agile and Transformation
AUGUST 21, 2023
I am writing today’s blog post from Tucson, where I wrote the epilogue to Digital Trailblazer. “I’m taking a different type of walk today, a hike actually, on one of the trails winding through Saguaro National Park in Tucson, Arizona,” is how I opened the chapter where I reflect on my journey writing the book.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Week
AUGUST 23, 2023
There’s more change in store for IT professionals, thanks to developments in tech and business strategies. See how you can thrive.

IT Toolbox
AUGUST 22, 2023
The three stages of network automation adoption. The post A Guide to Converting Network Automation Skeptics appeared first on Spiceworks.

Advertiser: GEP
Scope 3 emissions – which account for 70 – 80% of an organization’s emissions – are complex and multifaceted. They form the bulk of an organization’s environmental impact. It’s no surprise that enterprises still struggle to track and manage these emissions. '10 Practical Steps to Reduce Scope 3 Emissions' guides you through the essential phases of identifying, analyzing, and mitigating these emissions.

Forrester IT
AUGUST 25, 2023
In July 2023, we attended the Esri User Conference in San Diego, which with 20,000 attendees is the world’s largest geographic information systems (GIS) conference. The conference allowed consumers of GIS like National Oceanic and Atmospheric Administration (NOAA) and Exxon Mobil to demonstrate use cases where they applied those solutions.

Anoop
AUGUST 25, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Use Memory Integrity System Readiness Scan Tool in Windows 11 appeared first on HTMD Community Blog #1 Modern Device Management Guides by Alok Kumar Mishra.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

IT Toolbox
AUGUST 23, 2023
The industry needs mobile private networks to reach the next level. Here’s why. The post Unlocking IoT’s Potential with Mobile Private Networks appeared first on Spiceworks.

Forrester IT
AUGUST 23, 2023
On August 14, 2023, a Montana state court found that Montana violated the plaintiffs’ constitutional right to a “clean and healthful environment” by promoting the use of fossil fuels without factoring for the effects of greenhouse gas emissions (GHE). It sets legal precedent for similar cases already filed in other states.
Anoop
AUGUST 23, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Block Screenshots for Android Devices using Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar.

Information Week
AUGUST 21, 2023
Finance, transportation, government, and retail are examples of where a hybrid data warehousing approach can become useful. But there are challenges and complexities to overcome.

Advertisement
The complexity of financial data, the need for real-time insight, and the demand for user-friendly visualizations can seem daunting when it comes to analytics - but there is an easier way. With Logi Symphony, we aim to turn these challenges into opportunities. Our platform empowers you to seamlessly integrate advanced data analytics, generative AI, data visualization, and pixel-perfect reporting into your applications, transforming raw data into actionable insights.
IT Toolbox
AUGUST 25, 2023
Investments in cybersecurity initiatives are primarily driven to avoid risk and unnecessary costs. The post In the Line of Fire: Understanding and Conquering Cybersecurity Risks appeared first on Spiceworks.

Forrester IT
AUGUST 24, 2023
Demand-side platforms (DSPs) are defined and confined by the acronym’s connotations. In 2007, when DSPs emerged, they coincided with the growth of real-time bidding, a practice since revealed to be rife with data leakage and brand safety concerns.

Anoop
AUGUST 22, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Deploy Unmanaged macOS App using Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar.

Tech Republic Security
AUGUST 24, 2023
This QR code phishing campaign is targeting multiple industries and using legitimate services such as Microsoft Bing to increase its efficiency and bypass security.

Speaker: Gary Dmitriev
Our upcoming webinar aims to demystify the process of selecting and implementing automation tools for financial institutes. This session will provide your roadmap for vetting potential solutions, focusing on due diligence, vendor assessments, and aligning technology with strategic goals. We’ll also address the critical issue of innovation fatigue, offering tips on maintaining enthusiasm and momentum for new initiatives.

IT Toolbox
AUGUST 25, 2023
With Google deciding on sun-setting Universal Analytics, here are GA4 courses that can help marketers upskill them. The post Top 7 Courses for Marketers to Master Google Analytics 4 appeared first on Spiceworks.

Forrester IT
AUGUST 24, 2023
Cyber insurance is a common tool for risk transfer today. It’s also a key driver for cybersecurity program investment today. But who has cyber insurance and what benefits do organizations see from it?

Anoop
AUGUST 23, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Restrict Unauthenticated RPC Clients Policy using Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Abhinav Rana.

Information Week
AUGUST 23, 2023
NeuEon CISO Candy Alexander shares highlights from her 30-year cybersecurity background aiding tech companies by improving their cyber risk and security programs through business alignment and previews her upcoming keynote presentation on our "Cyber Resilience 2023: How to Keep IT Operations Running No Matter What" live virtual event on Thursday, Aug. 24.

Advertisement
Adding high-quality entity resolution capabilities to enterprise applications, services, data fabrics or data pipelines can be daunting and expensive. Organizations often invest millions of dollars and years of effort to achieve subpar results. This guide will walk you through the requirements and challenges of implementing entity resolution. By the end, you'll understand what to look for, the most common mistakes and pitfalls to avoid, and your options.

IT Toolbox
AUGUST 24, 2023
Unlock HR potential with data-driven insights for smarter decisions and strategic success. The post How to Develop HR Analytics Skills: A Comprehensive Guide appeared first on Spiceworks.
Forrester IT
AUGUST 22, 2023
Last month, Forrester announced its inaugural Security & Risk Enterprise Leadership Award. As former CISOs, my Forrester colleague Brian Wrozek and I are sharing our thoughts about why you should apply. There are tangible benefits to you, your team, your organization, and the greater security community.

Anoop
AUGUST 25, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post Configure Intune Win32 App Installation Time appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar.

Tech Republic Security
AUGUST 22, 2023
If you have users that need certain admin privileges on your Linux machines, here's a walk-through of the process for granting full or specific rights.

Advertiser: GEP
By 2027, Gartner predicts that 40% of sourcing will be handled outside of the procurement function. How can procurement pros ensure that the process is efficient and unified for all users? For a synchronized and democratized approach to procurement, leaders are embracing total procurement orchestration solutions. The What, Why and How of Total Procurement Orchestration details how a multi-level orchestration strategy streamlines procurement processes.

IT Toolbox
AUGUST 25, 2023
VMware Explore 2023 saw the company introduce exciting product upgrades and service announcements to support its multicloud and edge computing goal. The post VMware Explore 2023: Multicloud Solutions for Tomorrow’s IT Landscape appeared first on Spiceworks.

Forrester IT
AUGUST 21, 2023
Black Hat USA 2023: Insights From Our Short Vegas Residency Black Hat has gone from being RSAC’s smaller tech and practitioner-focused cousin to being a commercial showcase for cybersecurity vendors.

CIO Business Intelligence
AUGUST 21, 2023
Most CIOs and IT staffers remain, at heart, technologists, with many proclaiming their interest in shiny new tech toys. They may publicly preach “No technology for technology’s sake,” but they still frequently share their fascination with the latest tech gadgets. They’re not the only ones enthralled by tech. With technology and tech news now both pervasive and mainstream, many outside of IT — from veteran board members to college-age interns — are equally enthusiastic about bleeding-edge technol

Tech Republic Security
AUGUST 25, 2023
The Cisco Talos report exposes new malware used by the group to target Internet backbone infrastructure and healthcare organizations in the U.K. and the U.S.

Advertisement
In the fast-moving manufacturing sector, delivering mission-critical data insights to empower your end users or customers can be a challenge. Traditional BI tools can be cumbersome and difficult to integrate - but it doesn't have to be this way. Logi Symphony offers a powerful and user-friendly solution, allowing you to seamlessly embed self-service analytics, generative AI, data visualization, and pixel-perfect reporting directly into your applications.
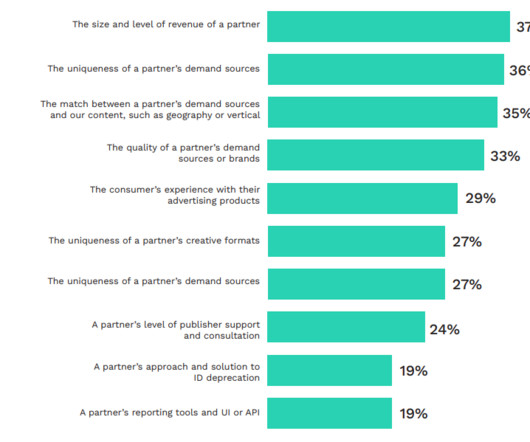
IT Toolbox
AUGUST 23, 2023
Regarding ID deprecation, most publishers don’t think current solutions like first-party data are enough to solve privacy-related and ID loss challenges. The post 57% of Publishers Are Most Concerned About the Current State of the Economy appeared first on Spiceworks.

Forrester IT
AUGUST 21, 2023
In the age of GenAI, vector databases are becoming increasingly important. They provide a critical capability for storing and retrieving high-dimensional vector representations, essential for supporting LLMs. Unlike traditional databases that are optimized for exact matches, vector databases are designed to support similarity searches.

Information Week
AUGUST 24, 2023
The fundamental people skills -- or chops -- are communicating, collaborating, being a team player, and listening, with the ultimate goal as connecting.

Tech Republic Security
AUGUST 24, 2023
A new study by Critical Insight shows that cybersecurity attacks in the health care sector are hitting more individuals and finding vulnerabilities in third-party partners.

Advertiser: Procom Services
From streamlining the job search process to efficiently navigating the influx of applications, AI-powered tools can revolutionize your recruitment efforts. By combining the efficiency of AI with the expertise of experienced recruiters, you can identify the ideal candidates who not only possess the necessary skills but also align with your company culture.
Let's personalize your content