How to improve delivery of 5G services and applications – without changing core infrastructure
TM Forum
OCTOBER 26, 2022
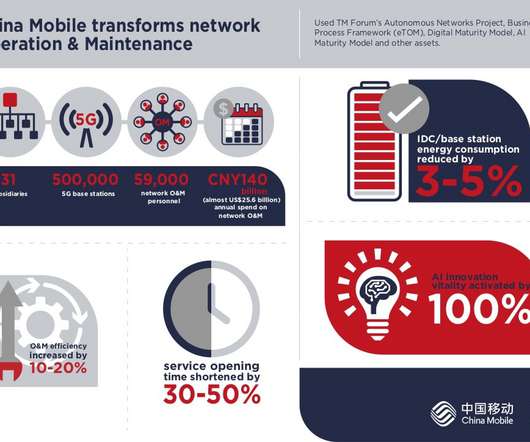
Among the promises of the 5G era is a range of entirely new, sector-specific digital services, achieved via advanced network technologies such as network slicing and multi-edge computing – which require consistently high performance and agile connectivity. changes to existing 5G core infrastructure.













































Let's personalize your content