Using X.509 Certs for DID Provenance
Phil Windley
APRIL 25, 2024
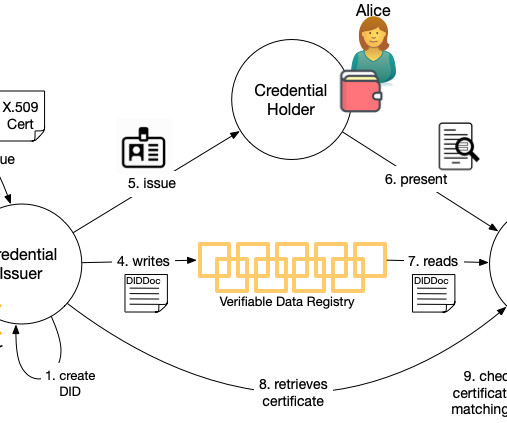
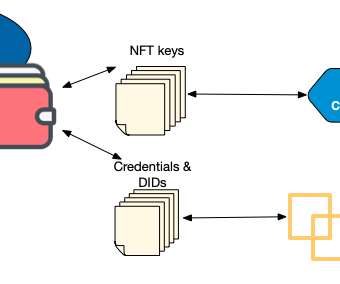
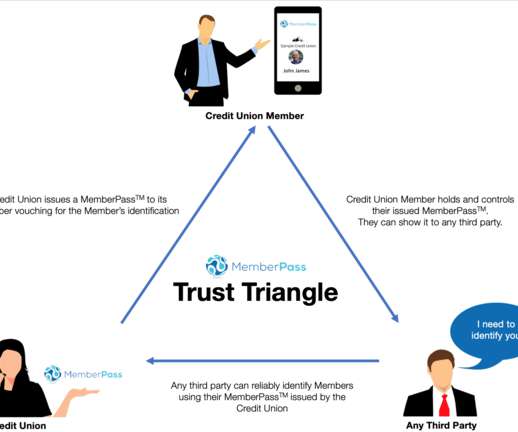
When you used a verifiable credential to prove something about yourself, the verifier can know cryptographically: (1) the identifiers for the issuer, (2) the credential hasn't been tampered with, (3) the credential was issued to you, and (4) the credential hasn't been revoked. Summary: The abundance of X.509











































Let's personalize your content