Trusona: Passwordless two-factor authentication
CTOvision
JUNE 22, 2019
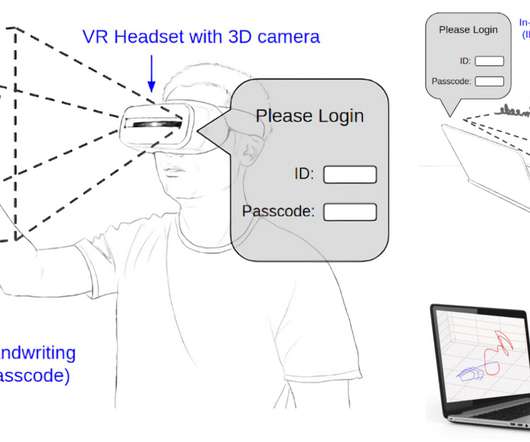
Trusona is the pioneer and leader in passwordless two-factor authentication (2FA). For a good overview and really fast demo of the power of Trusona see this video: Over 200 organizations, including some […].



















































Let's personalize your content