Adding Security Keys to Your Authentication Toolbox
SecureWorld News
JANUARY 10, 2024
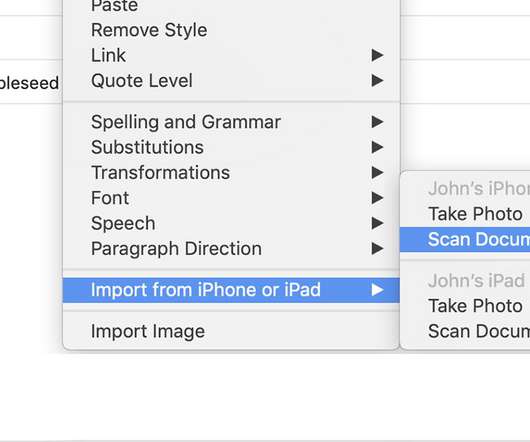
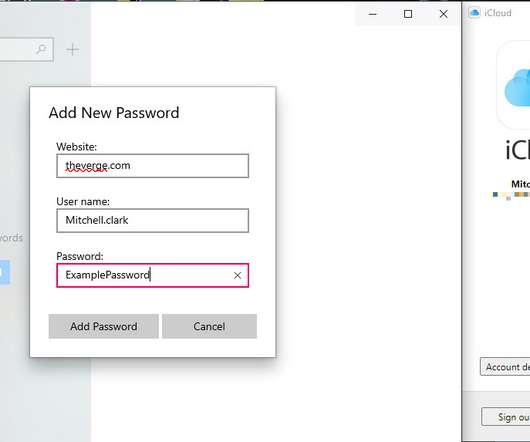
A quick intro to security keys: A security key can work in place of other forms of two-factor authentication such as receiving a code through SMS or pressing a button in an authentication app. When it came to authenticating, both keys worked just fine. Then, you enter your password and that's that.














































Let's personalize your content