Adobe is adding its ‘content authenticity’ tool to the latest Photoshop beta
The Verge
OCTOBER 20, 2020
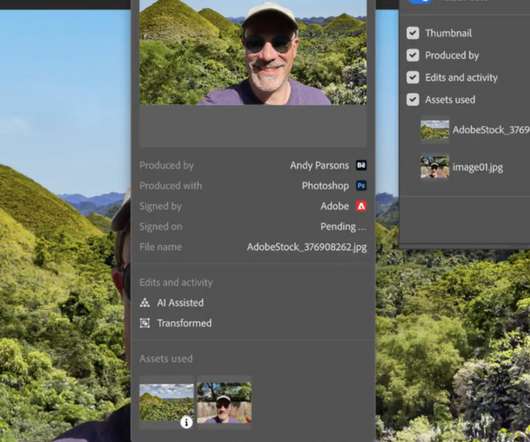
Adobe will let some Adobe Creative Cloud customers try a tool that builds trustworthy attribution directly into a picture. As part of a bigger software update, Adobe is moving forward with the Content Authenticity Initiative, a system it proposed last year.

















































Let's personalize your content