OpenHaystack is a new open-source tool that lets you create DIY AirTags on Apple’s Find My network
The Verge
MARCH 4, 2021
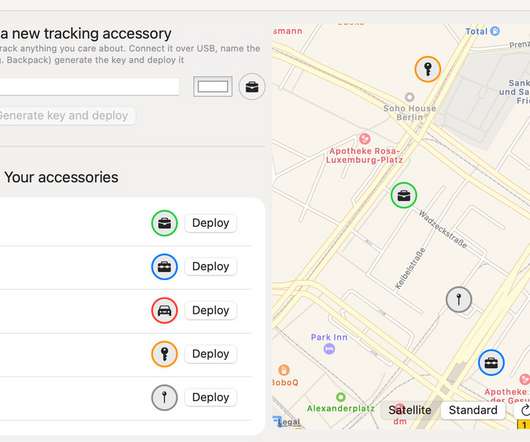
But ahead of that, there’s a new tool that will let anybody make their own Bluetooth tracking tag to use with the Find My network so they can track its location. Once registered on Apple’s Find My network, the OpenHaystack app will be able to report the tag’s location just like Apple’s Find My app works for iPhones and other Apple devices.












































Let's personalize your content