New Video: Automating Your Cyber Defenses Including Malware Removal
CTOvision
JUNE 21, 2014
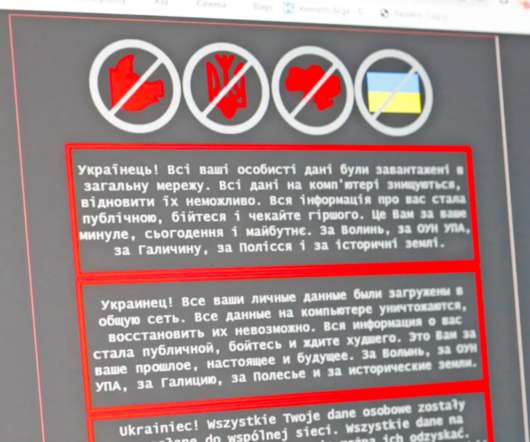
The video at this link and embedded below provides an overview of conclusions from CTOvision research into ways to automate the removal of cyber threats (including malware) from your enterprise. Additional context into this topic is available in our research report downloadable here: . By Bob Gourley. This paper.
















































Let's personalize your content