100+ critical IT policies every company needs, ready for download
Tech Republic Security
APRIL 14, 2021
From remote work and social media to ergonomics and encryption, TechRepublic has dozens of ready-made, downloadable IT policy templates.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Tech Republic Data Center
DECEMBER 17, 2023
The global population of internet and social media users grows each day, which means that the volume of shared data is also on a remarkable rise. Statista forecasts that the amount of data to be created, captured, copied and consumed globally by 2025 will be more than 181 zettabytes. With new capabilities rapidly emerging in.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Forrester IT
APRIL 29, 2021
million downloads since it debuted last year, according to Sensor Tower. Responding to this initial success, leading social media companies such as […]. Since posting our top 64 channel podcasts in 2019, there has been explosive growth in podcast adoption.

IT Toolbox
APRIL 16, 2024
A third-party telephony provider of Cisco suffered a breach wherein they hacked into and downloaded message logs for authentication SMS messages sent for Duo Security. The stolen data puts customers at risk of social engineering attacks to trick them into revealing credentials, carrying out financial fraud, etc.

Advertisement
Social platforms are now becoming mainstream contact center channels. Download this guide today to learn how to help your business adapt to this evolving landscape and leverage the power of next-generation digital customer service. However, customers are rapidly moving beyond these channels, seeking next-generation options.

SecureWorld News
FEBRUARY 15, 2024
The hackers rely heavily on social engineering tactics to distribute the malware. Android users were directed to fake app store pages to download infected apps. Uncovered by cybersecurity firm Group-IB , GoldPickaxe exists in both Android and iOS versions and was developed by a suspected Chinese hacking group called "GoldFactory."

Dataconomy
FEBRUARY 12, 2024
DignifAI is gaining attention in the social media lately. The tool is gaining attention in the social media lately ( Image credit ) While some view #DignifAI as a mere provocation, it aligns closely with the #tradwife movement, advocating for a return to traditional, restrictive gender roles. Download Python 3.6

Gizmodo
DECEMBER 10, 2020
Parler, the social media platform where Ted Cruz is free to dance naked under the cursed moon in the realm of the possessed, may not be the right-wing free speech utopia of the future. Despite offering a perfectly fine refuge for conservatives b g about Facebook and Twitter and YouTube’s moderation policies,… Read more.

Venture Beast
JULY 20, 2021
Grand Theft Auto Online is getting a combat-free social space with the Los Santos Tuners update available as a free download today. Read More.
Venture Beast
FEBRUARY 18, 2021
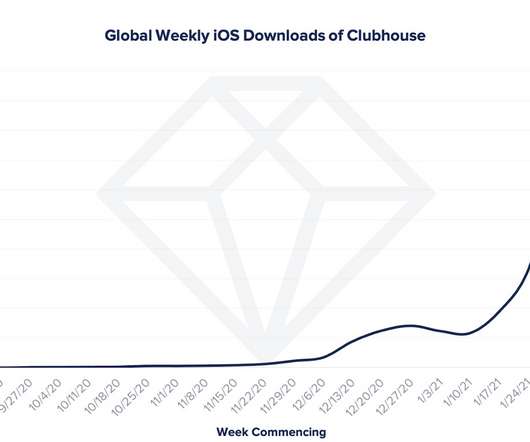
Clubhouse has exceeded 8 million downloads worldwide since launch, according to mobile insights and analytics firm App Annie. Read More.
Venture Beast
FEBRUARY 9, 2021
Hypercasual mobile game publisher SayGames has more than 2 billion downloads and it is starting a $10 million developer growth program. Read More.

Venture Beast
JUNE 19, 2021
billion downloads and 300 employees. Cyprus-based Azur Games has grown its hypercasual games business to more than 1.5 Read More.
Venture Beast
NOVEMBER 22, 2021
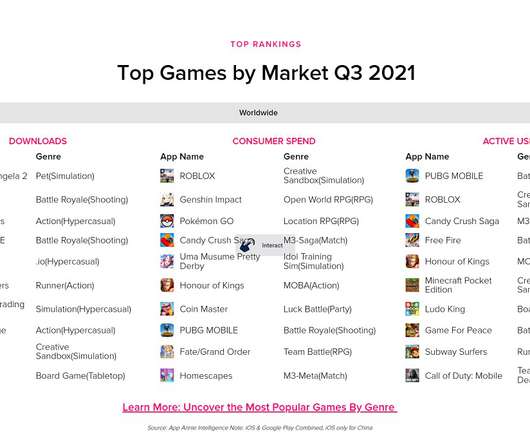
Consumers downloaded 14.3 billion games in the third quarter, including 3.6 billion hypercasual games, according to App Annie. Read More.

The Verge
APRIL 5, 2022
Block, the parent company of products like Cash App and Tidal, said in an SEC filing that a former employee downloaded “certain reports” that “contained some US customer information” without permission from Cash App Investing ( via Protocol ).

Venture Beast
JUNE 23, 2020
Call of Duty: Mobile has hit 250 million downloads since its debut on October 25, according to mobile measurement firm Sensor Tower. Read More.

Venture Beast
MAY 4, 2021
Call of Duty: Mobile has crossed 500 million downloads worldwide since its launch in October 2019. It has also crossed $1 billion in spending. Read More.
Gizmodo
MARCH 12, 2022
To prepare for these situations, you might want to download YouTube videos in advance for offline viewing. Watching YouTube videos is all well and good while you’ve got a stable internet connection, but there might be times when you don’t have a high-speed link to the web—on vacation, on your travels, on your commute. Read more.

The Verge
APRIL 7, 2021
Twitter’s already building a competitor to the hot social audio app Clubhouse, but apparently, it’s discussed outright acquiring the company, too. It’s also unclear whether Twitter or Clubhouse approached the other first, which could speak to how either platform is feeling about the competition in the social audio space.
Venture Beast
JULY 1, 2020
The title has been downloaded more than 2 million times and has been No. 1 in the iOS App Store for a few days -- even ahead of free app leader TikTok. Read More.

CTOvision
JULY 10, 2015
You can measure practically anything in the age of social media, but if you don’t know what you’re looking for, collecting mountains of data won’t yield a grain of insight. Download or order here.

GeekWire
MARCH 23, 2021
We are one of many, and we’re excited to add a consumer social company to that mix.” Year-over-year revenue growth of 566% was fueled in part by the pandemic and trends toward social gatherings online. Gaming company or social company? I think in a lot of ways gaming is the new social.”

Dataconomy
JULY 19, 2023
The WormGPT download can be easy, but there are many consequences await you at the end of the road. The WormGPT download process has its ups and downs ( Image Credit ) WormGPT download: What does it offer? The WormGPT download process is very dangerous and brings its own consequences.

The Verge
DECEMBER 2, 2020
2020 was a year when people around the world were forced to find new ways to connect, and that trend is clearly visible when you look at the most downloaded apps on Apple hardware. The mobile version is particularly popular since it’s free to download. You can check out the full most-downloaded list below: Top free iPhone apps.

Venture Beast
JULY 31, 2020
Thatgamecompany said its Sky: Children of the Light mobile game has topped 35 million downloads, and the company is selling Sky's digital soundtrack now. Read More.
The Verge
JULY 19, 2021
Two of the earliest employees behind WhatsApp have emerged with a new private social network called HalloApp. Starting Monday, anyone can download and sign up for HalloApp in Apple’s App Store and Google Play on Android devices. A screenshot of HalloApp. They both worked at WhatsApp before and after Facebook bought it for $22 billion.
GeekWire
MARCH 10, 2021
Limit is a social media app for people between the ages of 18 and 25. He’s just trying to limit the age range for people who can use his new social media product, which is fittingly called Limit App. Instead of a secret Instagram account to keep mom from peeping on your social life, Limit locks mom out. Limit App Images).
The Verge
JUNE 15, 2021
That’s the bet behind IRL, a young social network that has been quietly growing over the past year and just attracted an eye-popping amount of money to take on Facebook. According to Shafi, the goal is to become “a super messaging social network” over time. “We IRL’s groups and events can be accessed on its app or website. Image: IRL.

Gizmodo
MAY 9, 2021
Good news: The audio-based social network Clubhouse is finally bringing its app to Android after more than a year of iOS exclusivity, the company announced Sunday. Bad news: The beta is only available for U.S. users, and, just as with Clubhouse’s iOS version, it remains invite-only for now. So not just anyone can sign… Read more.

The Verge
FEBRUARY 16, 2022
Microsoft is removing all social hubs hosted in AltspaceVR and requiring users to log into the virtual reality app using a Microsoft account. The social hubs in AltspaceVR were designed “to help foster new friendships” and act as an entry point to get familiar with AltspaceVR itself. Microsoft acquired AltspaceVR in 2017.

The Verge
AUGUST 16, 2021
Yik Yak — the anonymous, local social media app that only shows posts from people in your immediate area — has returned from the grave with new ownership after shutting down four years ago. But while the anonymity made it popular for college students, Yik Yak also was rife with bullying and harassment.

Galido
OCTOBER 27, 2016
There are still a few free MP3 music download sites that are available. These sites will allow you to download music free of charge. Here are just a few of the MP3 music download sites that you should not miss: YouTube. Once you have downloaded the track, you can listen to the song whenever you want to. SoundCloud.
Forrester IT
JULY 6, 2023
This new app is garnering initial excitement and downloads, but it still has a long road ahead to scale and retain an audience, integrate new features, and eventually monetize through advertising. Last night, Meta launched its rival app to Twitter, Threads, in 100 countries.

Gizmodo
JUNE 25, 2021
El Salvador will give every adult citizen $30 in bitcoin, provided they download and register the government’s cryptocurrency app, known as Chivo, according to President Nayib Bukele. Read more.

Trends in the Living Networks
SEPTEMBER 24, 2009
Continuing our series of translations of Social Media Strategy Framework , today is German. See the original post for the full overview of the Social Media Strategy Framework in English. Click on image to download pdf. Please share this with any German speakers.

Trends in the Living Networks
SEPTEMBER 30, 2009
Continuing our series of translations of Social Media Strategy Framework , today is Dutch. See the original post for the full overview of the Social Media Strategy Framework in English. Click on image to download pdf. Please share this with any Dutch speakers who would be interested.

Trends in the Living Networks
SEPTEMBER 29, 2009
Continuing our series of translations of Social Media Strategy Framework , today we are launching the Spanish edition. See the original post for the full overview of the Social Media Strategy Framework in English. Click on image to download pdf. Please share this with any Spanish speakers who would be interested.

Trends in the Living Networks
MARCH 13, 2022
For many years my reputation and credibility as a futurist has been significantly supported by my 2002 book Living Networks , which anticipated many developments of the last two decades, including pointing to the rise of social networks and micro-messaging before any of today’s social platforms existed.

TechSpot
MARCH 1, 2021
Earlier this year, it was revealed that social media app Parler had been used as a means to organize the January 6 assault on the Capitol Building in Washington, DC. By downloading and archiving almost all of the data posted on Parler before it was booted off of Amazon Web.

Trends in the Living Networks
JULY 20, 2009
Today we launch our Social Media Strategy Framework. This provides guidance and a frame on how organizations can approach engaging with social media, following in the tradition of our highly popular frameworks such as Web 2.0 Click on the image to download pdf. Use social media yourself. Set clear social media policies.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?




Let's personalize your content