ForAllSecure Hosts CMU Open Source Software Hackathon
ForAllSecure
MAY 4, 2022
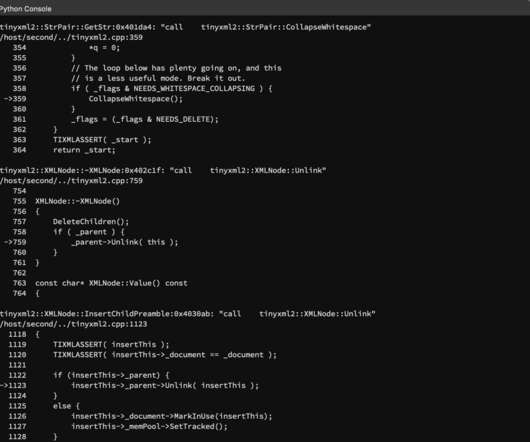
For the next three hours they integrated Mayhem Free into various open source software GitHub repositories. The purpose is to help ForAllSecure secure open source software. He then introduced a CMake example before giving the students exercises using open source fuzz testing tools such as AFL and libfuzzer.












































Let's personalize your content