Acceptance Networks for Self-Sovereign Identity
Phil Windley
FEBRUARY 6, 2024
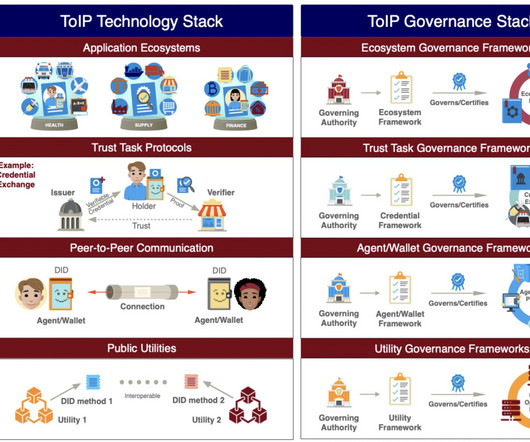
There's a name in the financial services industry for the network that reduces risk so that trust can be replaced with confidence: an acceptance network. Each component of the acceptance network plays a crucial role in ensuring that transactions are processed efficiently, securely, and accurately.






























Let's personalize your content