Managing the whole lifecycle for human and machine authentication
CIO Business Intelligence
AUGUST 17, 2022
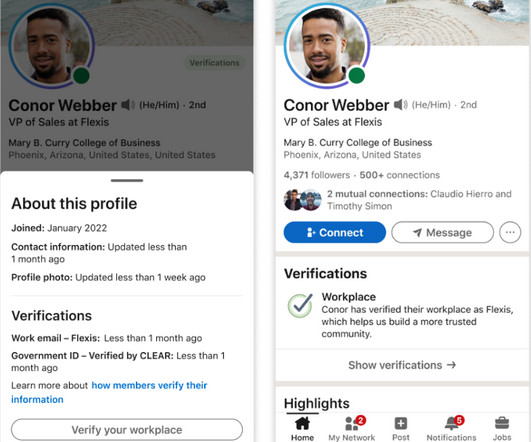
In my last column for CIO.com , I outlined some of the cybersecurity issues around user authentication for verification of consumer and business accounts. . FIDO as an industry initiative was set up a decade ago to standardize the need for strong authentication/password technologies. Well, yes, but there is more that tech pros can do.
















































Let's personalize your content