How Low-Code and No-Code Really Helps Reduce Tech Debt and Drive Innovation
Social, Agile and Transformation
MARCH 22, 2022
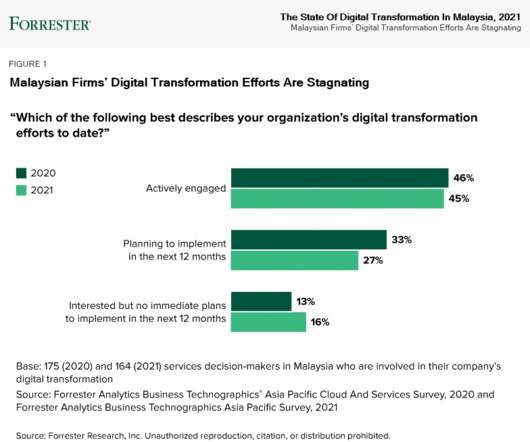
Are you feeling the impact of technical debt on accelerating DevOps, delivering innovations, and driving digital transformation? Recent research shows organizations are spending almost as much time addressing technical debt (28%) compared to running operations (38%) and building new capabilities (33%). Ouch. You already know that I am a strong proponent of citizen.









































Let's personalize your content