Our Contact Center Megatrend Predictions for 2023
Spearline Testing
DECEMBER 19, 2022
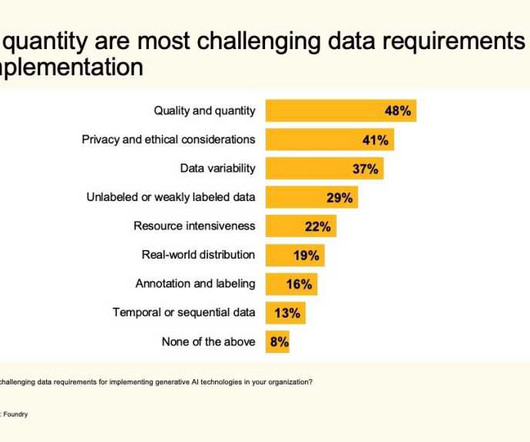
So now is a good time to think about the technologies that are going to be table stakes for 2023 and focus on the contact center trends that matter. They want to use their preferred medium to interact with you, and they don’t want to have to tell you the same things over and over across a multitude of platforms and applications.


















































Let's personalize your content