Google, Apple, Microsoft promise end to passwords, courtesy of your mobile phone
Tech Republic Security
MAY 5, 2022
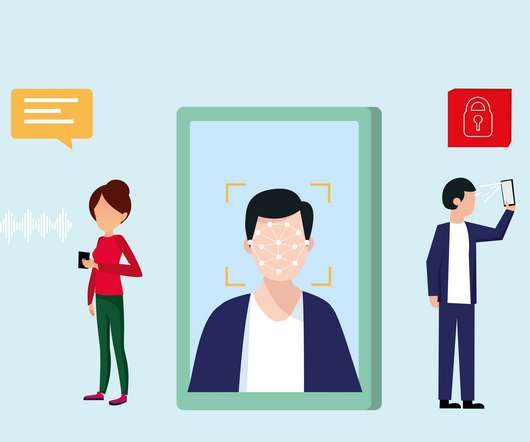
Adopting a new authentication method from the FIDO Alliance, the three major OS vendors will let you use encrypted credentials stored on your phone to automatically sign you into your online accounts. The post Google, Apple, Microsoft promise end to passwords, courtesy of your mobile phone appeared first on TechRepublic.














































Let's personalize your content