OpenHaystack is a new open-source tool that lets you create DIY AirTags on Apple’s Find My network
The Verge
MARCH 4, 2021
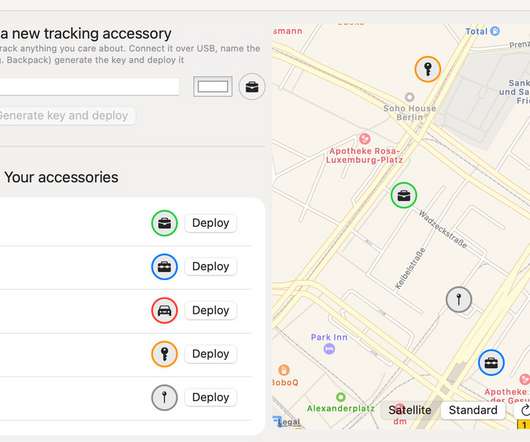
OpenHaystack is a new open-source tool developed by security researchers at the Secure Mobile Networking Lab , who have essentially reverse-engineered the way Apple devices register themselves to the Find My mesh network. That doesn’t mean you should just go ahead and start using OpenHaystack, however.
















































Let's personalize your content