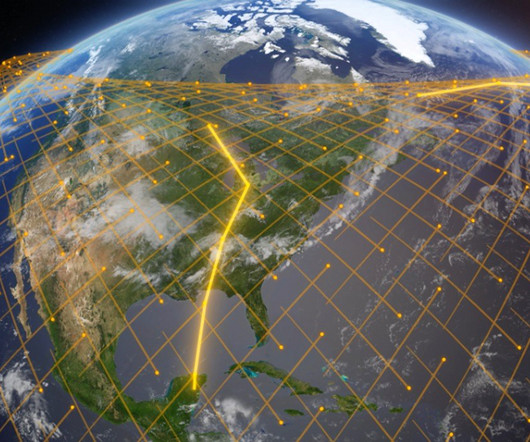
How Zero Trust is supposed to look
CIO Business Intelligence
DECEMBER 19, 2023
Over the last few years, it has become more and more apparent that the status quo for networking and security is no longer viable. Endlessly extending hub-and-spoke networks to more remote users, branch offices, and cloud apps increases risk, harms the user experience, and is prohibitively complex and expensive.










































Let's personalize your content