Rule-Based Programming and the Internet of Things
Phil Windley
JUNE 7, 2023
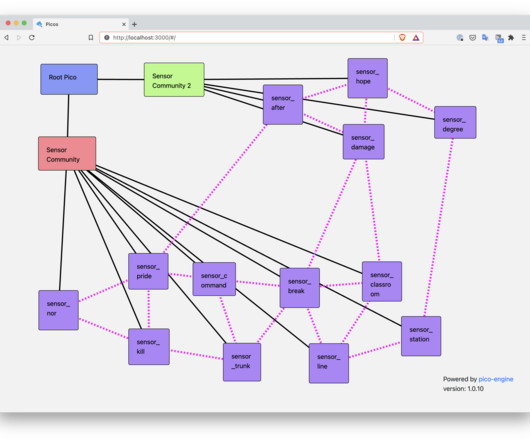
Picos are a rule-based system for programming in the Internet of Things (IoT). Rules are a good fit for IoT programming because so much of what happens with things is event-based. For example, an event that contains the temperature reported by a sensor might also report the sensor's batter level.


















































Let's personalize your content