HID Global Awarded ATEX, IECEX and UKEX Poly Tag™ Certifications
HID Global
OCTOBER 22, 2021
HID Global Awarded ATEX, IECEX and UKEX Poly Tag™ Certifications. Fri, 10/22/2021 - 11:07.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 tags certification
tags certification 
HID Global
OCTOBER 22, 2021
HID Global Awarded ATEX, IECEX and UKEX Poly Tag™ Certifications. Fri, 10/22/2021 - 11:07.
Phil Windley
APRIL 25, 2024
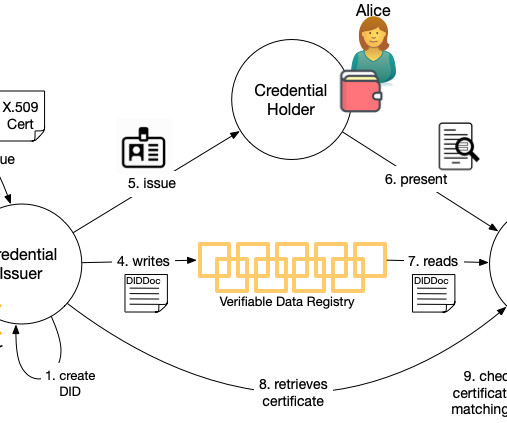
509 certificate authorities who already perform identity proofing for businesses provides a rich resource that can be leveraged to boot the verifiable data ecosystem. 509 certificates could help with this. 509 certificate providing TLS security. 509 certificate useful for checking the provenance of a DID lies in one key change.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Generative AI Deep Dive: Advancing from Proof of Concept to Production
Reimagining Cybersecurity Training: Driving Real Impact on Security Culture
Don’t Get Left Behind: Leveraging Modern Product Management Across the Organization
Phil Windley
MAY 28, 2021
509 certificates have been around for 40 years and have proven to be a trustworthy means of exchanging data. 509 certificates?" 509 is a standard that defines the format for public key certificates. 509 is a standard that defines the format for public key certificates. 509 certificate. 509 certificate.

Scott Lowe
JANUARY 19, 2024
Matt Gowie of MasterPoint explains terraform-null-label and its use in providing more consistent naming and tagging of cloud resources. Vivek Gite aka nixCraft explains how to check the expiration date of a TLS/SSL certificate from the command line. Career/Soft Skills Anyone thinking of getting a GitHub certification ?
Phil Windley
MAY 27, 2021
509 certificates have been around for 40 years and have proven to be a trustworthy means of exchanging data. 509 certificates?" 509 is a standard that defines the format for public key certificates. 509 is a standard that defines the format for public key certificates. 509 certificate. 509 certificate.

CIO Business Intelligence
DECEMBER 21, 2023
Workload segmentation using user-defined tags allows organizations to create custom security groups based on user-defined tags and native attributes on AWS. Comprehensive cloud coverage supporting major CSPs including support for Google Cloud Platform (GCP), Azure China Regions, and AWS GovCloud with FedRAMP certification.
The Verge
AUGUST 3, 2020
It’s similar to the standard EXIF tags that show the location or date of a photograph, but with cryptographic signatures that let you verify the tags haven’t been changed or falsely applied to a manipulated photo. Any CAI metadata tags will show that the image was manipulated, however.

Kitaboo
JULY 14, 2023
However, keep in mind that premium ebooks or specialized content may come with a higher price tag. Cost-Effectiveness over Time: E-learning courses offer structured learning experiences and certifications, making them more cost-effective over time. 4 Do e-learning courses and ebooks offer certifications?

Scott Lowe
OCTOBER 12, 2021
Specific resources used by the cluster must have certain AWS tags assigned to them. Tagging Cluster Resources. The “Getting Started” page on the Kubernetes AWS Cloud Provider site only says this about tags: Add the tag kubernetes.io/cluster/ elb: 1 tag, while private subnets need a kubernetes.io/internal-elb:

SecureWorld News
SEPTEMBER 25, 2021
In a blog post, Neel Mehta, Information Security lead for Google, explains how a hacker has managed to break certificate code parsing to invade email inboxes and infect users with malware. 509 certificate.”. Google recently landed on one of these techniques while tracking hackers in this ongoing game of cat-and-mouse.

Phil Windley
NOVEMBER 2, 2022
These registrations, from which our modern system of birth certificates springs, became the basis for personal identity and legal identity in a way that conflated these two concepts. Birth certificates are a source of legal identity and a proof of citizenship, and thus the basis for individual identity in most countries.

The Verge
JANUARY 15, 2021
price tag (which varies by model). It’s a quick and easy way to get users the fully certified experience without having to wait for certification (and without Apple’s Made For iPhone program fees). The only thing missing is MagSafe certification, meaning Apple will only let your phone charge at 7.5W.

CIO Business Intelligence
FEBRUARY 14, 2024
The other problem is gen AI tools and users not seeing information that should be included because the metadata tagging and sensitivity labels haven’t been correctly applied to the data. Containers and certificates Privilege management depends on identity management, another area that demands continued attention.

Scott Lowe
OCTOBER 12, 2021
Specific resources used by the cluster must have certain AWS tags assigned to them. Tagging Cluster Resources. The “Getting Started” page on the Kubernetes AWS Cloud Provider site only says this about tags: Add the tag kubernetes.io/cluster/ elb: 1 tag, while private subnets need a kubernetes.io/internal-elb:

Scott Lowe
FEBRUARY 18, 2020
In this post, I’ll share information provided to me by a reader, Christian Del Pino, about setting up Kubernetes on AWS with kubeadm but using manual certificate distribution (in other words, not allowing kubeadm to distribute certificates among multiple control plane nodes). Manually Distributing Certificates.

Dataconomy
MAY 6, 2024
It is marked with the ‘Remembering’ tag which appears next to the name and doesn’t appear in public spaces like user suggestions. Memorialized accounts have the ‘Remembering’ tag next to the user’s name and preserve their digital presence to friends and family.

Linux Academy
JUNE 4, 2019
The AWS DevOps Professional Certification Exam has recently been updated and has a new emphasis on the AWS Developer Tools suite. TagsLists all tags in the local repo: git tag. Pulls all tags from the CodeCommit repository to the local repo: git fetch --tags. What is AWS Developer Tools? How do I start?

Linux Academy
FEBRUARY 1, 2019
When Microsoft announced all-new Azure certification exams last September, we added four new Training Architects focused on preparing our students. Linux Academy is the only way to get exam-like training for multiple Microsoft Azure certifications. New Hands-On Azure Training Courses. Creating and configuring VNet peering and DNS.

Scott Lowe
AUGUST 14, 2019
Resources used by the cluster must have specific AWS tags assigned to them. Assigning Tags to Resources. The AWS cloud provider needs resources to be tagged with a tag named kubernetes.io/cluster/ If you don’t know the SHA256 hash of the CA certificate, see this post. cluster/ (the value is immaterial).

GeekWire
MARCH 14, 2024
This month, the company expects to submit to the Nuclear Regulatory Commission an application for the certification of its Natrium reactor , which it developed with GE Hitachi Nuclear Energy. Levesque declined to provide an updated price tag for the Kemmerer project.

Phil Windley
JULY 5, 2021
But what if, in some future world, the root certificate authority of the identity documents I use for banking, shopping, travel, and a host of other things decides to revoke my identity for some reason? Tags: identity ssi didcomm ssiot. I wrote: If Fitbit decides to revoke my account, I will probably survive.

Linux Academy
JULY 1, 2019
Here’s what we have for our early access: Puppet Professional Certification – PPT206 – We will cover everything from basic module authoring to setting up multi-master environments that allow us to push code across massive infrastructures and manage our hosts with features, such as Code Manager, Bolt, and PuppetDB.
GeekWire
JANUARY 4, 2024
They didn’t share a price tag for the initiative and don’t have a planned capital campaign to fund the project. But the future is clearer for Brightwork, which was called W27 in earlier plans. Here are some details: Brightwork will be an 11-story structure with 345,000 square feet of leasable space located at Brooklyn Ave.

GeekWire
AUGUST 16, 2023
The price tag spiked after engineers realized the foundation work would be much more difficult and as inflation drove up building supply costs, Lise said. The center will be highly environmentally efficient, aiming for Living Building Challenge certification.

Phil Windley
FEBRUARY 7, 2022
An easy way to think about self-certification is that it describes systems (and protocols) that don't rely on third parties. Closely related to the idea of self-certification is self-administration. Tags: web3 ssi identity keri decentralized+identifiers. Photo Credit: Bison calf suckling from Frank Schulenburg (CC BY-SA 4.0).

Phil Windley
MARCH 25, 2020
In a recent Gates Foundation AMA on Reddit , Bill Gates said the following in response to a questions about the impact of Covid-19 on businesses: Eventually we will have some digital certificates to show who has recovered or been tested recently or when we have a vaccine who has received it.

Scott Lowe
AUGUST 22, 2013
They automatically generate some self-signed certificates you’ll need later. NVP uses self-signed certificates to authenticate hypervisors, so you’ll need to be sure that the certificates have been generated (they should have been generated during the installation of OVS). Adding the Hypervisor to NVP. Click Save.

Phil Windley
DECEMBER 2, 2020
Of course, we could also solve this problem with digital certificates. The advantage of using SSIoT for secure firmware updates instead of digital certificates is that if Baratza is using it for other things (see below), they get this for free without also having to support the certificate code in their products or pay for certificates.

Linux Academy
JUNE 28, 2019
By passing the exams and obtaining this badge, you’ll demonstrate your ability to properly develop a basic Chef cookbook, and be on your way to obtaining the Chef certification. Puppet Professional Certification – PPT206. Tag images and push them to Docker Hub. Difficulty Level: Advanced.

I'm not lost, I'm wondering
JULY 29, 2008
Interesting-looking indirect critique of university certification. tags: accountability , universities. On Accountability, Consider Bologna :: Inside Higher Ed :: Higher Education’s Source for News, Views and Jobs.

Linux Academy
APRIL 30, 2020
” Or if a learner mentioned certification we always emphasized the achievement over the method. Apart, neither platform was truly “better” We were merely chasing one another’s shadows in an infinite game of tag. Learners would sheepishly approach our booth with ACG swag and say “I love you guys!

Phil Windley
MARCH 27, 2023
Rather than using certificates, it manages keys automatically and beneath the covers, so it’s as user-friendly as possible. Tags: fido identity authentication passkeys I liked how she described the security provisions of passkeys (also know as Fast ID Online or FIDO). This makes FIDO an easy, inexpensive way for people to authenticate.

A Screw's Loose
APRIL 10, 2013
They set up an identity system that allows them to issue a certificate to each user per device. If a user has a laptop and a tablet, they will receive a certificate on both. The certificate should hopefully have the device type as part of it (this allows more policy based actions on the data). Tags Applications.

Galido
APRIL 17, 2019
A predefined reply is provided as tags during an email reply. It also awards certificates on completion so that you can upgrade your CV and get an AI job. Email Response. AI also helps you to respond to your emails in an essay and quick way by analyzing your email contents. In-Home Devices.

A Screw's Loose
AUGUST 28, 2012
They may choose to do straight authentication against your enterprise id system, could use a certificate to do the same thing, or go with a token provided through oauth or SAML. print Tagged as: Enterprise Mobility , MIM , Security. Tags Applications. In this description though, we are looking at MAM, not MIM. Recent Posts.

Linux Academy
MAY 31, 2019
In today’s technology landscape, s ecurely storing and controlling things like passwords, certificates, tokens, and encryption keys, is a necessary, but complicated challenge. For the tag, name this Server-Vault. To help with this challenge, a number of different tools and technologies have been developed.

Phil Windley
MARCH 29, 2022
One of the plot points involves using certificate authorities (CA) for censorship. To review briefly, certificate authorities are key players in public key infrastructure (PKI) and are an example of a core internet service that is distributed and hierarchical. Root certificates are held in browsers or operating systems.

Phil Windley
JULY 14, 2018
And you likely have a relationship with the state, and credentials they issue representing your birth certificate or drivers license. Tags: byu sovrin india identity aadhaar. Similarly, you could have a relationship with your employer and an employer-issued credential stating you're an employee. The list goes on.

Scott Lowe
FEBRUARY 27, 2014
Set the display name and (optionally) add one or more tags to the service node object. On step 4 (Credentials), you’ll need the SSL security certificate from the service node. Since you have established network connectivity to the service node, just SSH into the new service node and issue show switch certificate.

Scott Lowe
FEBRUARY 18, 2019
Kubernetes-specific tags on resources needed by the cluster. In that post, I listed four key configuration items that are necessary to make the AWS cloud provider work: Correct hostname (must match the EC2 Private DNS entry for the instance). Proper IAM role and policy for Kubernetes control plane nodes and worker nodes.

ForAllSecure
APRIL 7, 2021
And it's not getting better in 2019 is certification organization ISC squared, released a study showing the extent of the problem here CNBC. I've got a lot of industry certifications, but having all those paper degrees proved to be a poor equivalent to having actual hands on experience in information security.

ForAllSecure
APRIL 7, 2021
And it's not getting better in 2019 is certification organization ISC squared, released a study showing the extent of the problem here CNBC. I've got a lot of industry certifications, but having all those paper degrees proved to be a poor equivalent to having actual hands on experience in information security.

A Screw's Loose
OCTOBER 28, 2011
Something that, if it was going to replace the Blackberry, had encryption and could use certificates and the like. You would be able to use corporate wireless with hidden SSIDs and they would accept certificates to prove the device belonged to who it said it did. Tags Applications. allowed a numerical pin only). Categories.

The Verge
SEPTEMBER 5, 2020
Apple has tagged that “Bionic” moniker to the A11 and A12 as well, so perhaps we’ll be seeing an A14 Bionic this year. We may also have an idea about the battery sizes for the new phones, thanks to reported certifications. This year’s iPhones are launching later than normal. The rumored 5.4-inch inch iPhone might get a 3687mAh pack.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content