Authenticating With Your API
ForAllSecure
OCTOBER 6, 2022
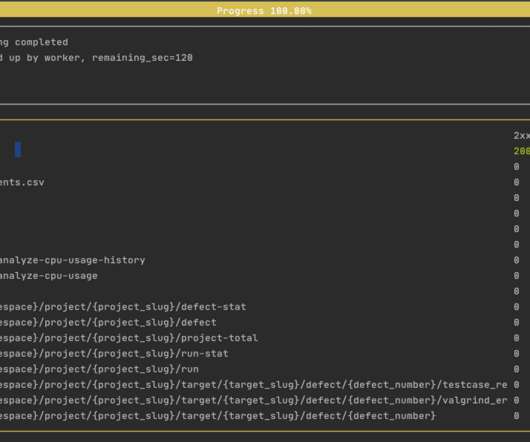
For most APIs, the next step is setting up authentication. After all, without successfully authenticating, Mayhem for API can only test for very superficial problems! Giving the fuzzer a way to authenticate to the target API will enable it to exercise more endpoints and maximize coverage. Basic Authentication.



















































Let's personalize your content