Documents Unsealed: North Korea's Global Hacking Campaign
SecureWorld News
FEBRUARY 18, 2021
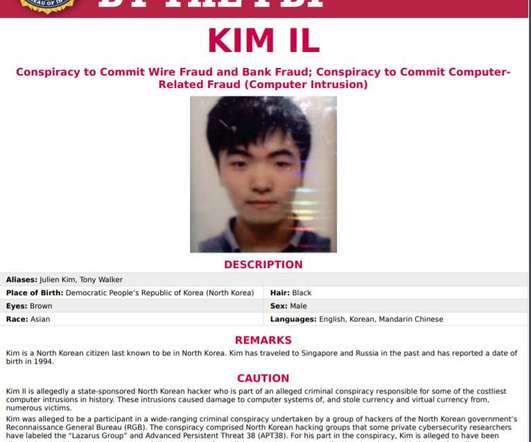
In court documents unsealed this week, the United States Department of Justice revealed its hand to show new evidence. The unsealed documents highlight a number of attack targets and motives in an effort to hack, digitally intrude, and defraud. The list goes on. Demers of the DOJ's National Security Division. global targets.















































Let's personalize your content