Windows 11 is here: Key points to know as Microsoft rolls out its new operating system
GeekWire
OCTOBER 4, 2021
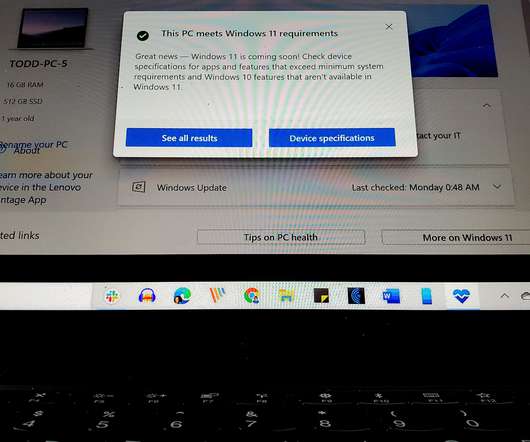
Windows 11 is a free upgrade for computers and tablets running Windows 10, the operating system that Microsoft first released more than six years ago. Windows 11 brings a refreshed user interface, better performance and security, and a variety of new features. 5, the official launch day.

















































Let's personalize your content