Radically simplify and expand Zero Trust to cloud workload
CIO Business Intelligence
DECEMBER 21, 2023
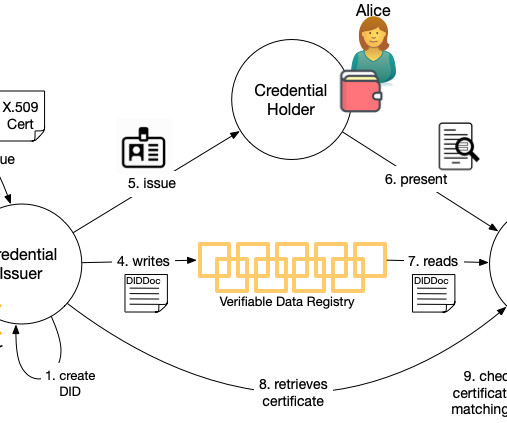
To address these challenges, organizations need a simple and automated approach based on zero trust architecture to deliver robust security as dynamic workloads move across on-prem data centers and multi-cloud environments. Zscaler Fig 1: Zscaler Zero Trust Cloud Connectivity.











































Let's personalize your content