From edge to cloud: The critical role of hardware in AI applications
CIO Business Intelligence
JUNE 6, 2023
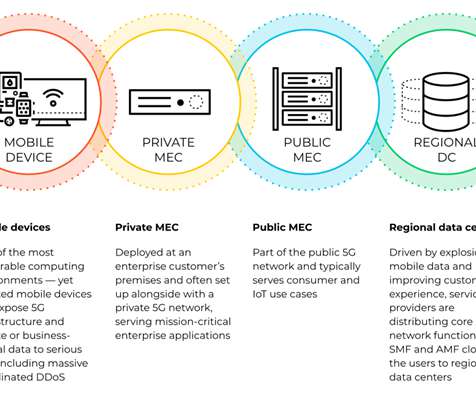
The world has woken up to the power of generative AI and a whole ecosystem of applications and tools are quickly coming to life. It is becoming increasingly important in various industries, including healthcare, finance, and transportation. Hardware innovations become imperative to sustain this revolution.













































Let's personalize your content