Scener sees growth in social streaming as startup set to host virtual Comic-Con screenings
GeekWire
JULY 16, 2020
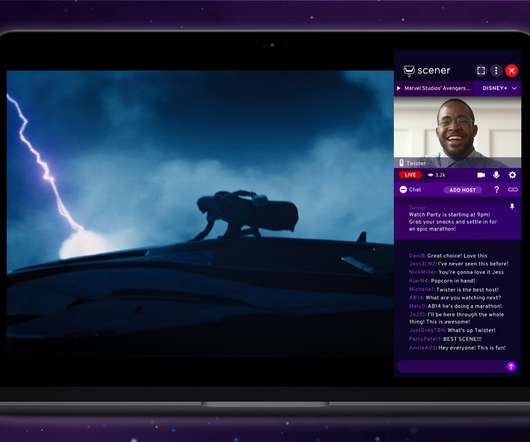
Scener , the RealNetworks spinoff that lets people connect and interact virtually while watching their favorite streaming content, is expanding its platform as it experiences substantial growth during the coronavirus pandemic. Scener is capitalizing on lockdowns during the ongoing health crisis and the desire for social gatherings.
















































Let's personalize your content