I was a virtual NBA fan: What it’s like to cheer from the digital sidelines in Microsoft Teams
GeekWire
AUGUST 21, 2020
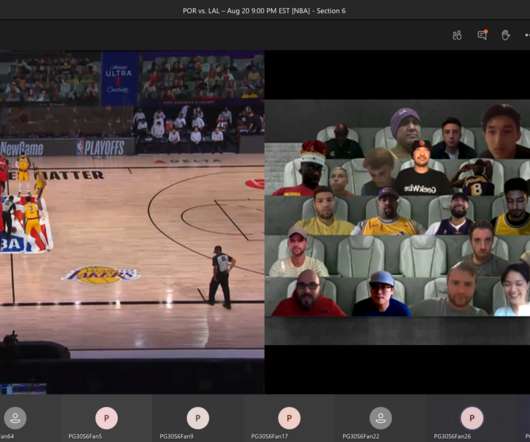
This is the spectator view for fans watching NBA games “courtside” in Microsoft Teams: the live stream on one side, and your virtual cheering section on the other. My big takeaway: Microsoft and the NBA are on to something with their new tech-fueled virtual fan experience. Look out for me in the virtual stands!!!




































Let's personalize your content