This startup aims to improve recycling by capturing ‘chemical fingerprints’ with high-tech cameras
GeekWire
APRIL 25, 2023
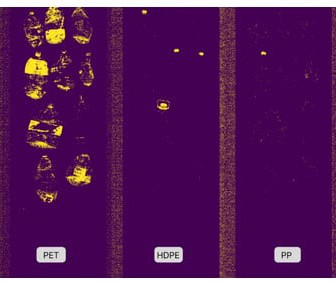
Metaspectral uses hyperspectral cameras to rapidly create a chemical fingerprint of plastic items, distinguishing between polyethylene terephthalate (PET), high-density polyethylene (HDPE), and polypropylene (PP) plastics. “It allows us to make up a chemical fingerprint off the material we’re looking at.”


















































Let's personalize your content