Why Retailers Must Avoid Passwords
HID Global
APRIL 1, 2024
Discover how RFID reader technology revolutionizes retail with secure, passwordless authentication for enhanced efficiency and security. Learn more.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

HID Global
APRIL 1, 2024
Discover how RFID reader technology revolutionizes retail with secure, passwordless authentication for enhanced efficiency and security. Learn more.

GeekWire
JANUARY 20, 2024
Plus, our colleague Taylor Soper’s deep dive into the downfall of Zulily bolsters a not-so-far-fetched hypothesis about the motives of the private equity firm that acquired and ultimately shut down the online retailer.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

SecureWorld News
AUGUST 25, 2023
Common Labor Day scams to watch out for Fake Retail Promotions: Cybercriminals create counterfeit websites or email campaigns that mimic legitimate retailers offering massive discounts on popular products. Email Filters and Authentication: Implement robust email filters that can identify and quarantine phishing emails.

CIO Business Intelligence
MAY 2, 2022
Password-based authentication is likely the most widely used method of authenticating users to online services. Password-based authentication is used because it is easy to understand and implement. They provide multifactor authentication (MFA) without the usual burden on the user. on a user’s other online accounts.

ComputerWorld IT Management
JUNE 20, 2016
Retailers have this love-hate relationship with EMV, in that they love to hate EMV. With that in mind, it's easy to understand why major retailers — Walmart last month and Home Depot last week — are suing Visa and MasterCard in an attempt to fight chip cards any way they can. Of course, the retail argument isn't quite phrased that way.

CIO Business Intelligence
OCTOBER 16, 2023
Okta issued an alert to clients in late August warning about incoming threats by hackers to gain access to “manipulate the delegated authentication flow via Active Directory (AD) before calling the IT service desk at a targeted organization, requesting a reset of all MFA factors in the target account.” Ransomware, Security

CIO Business Intelligence
JULY 10, 2023
It can often feel as though trust and authenticity are in short supply these days. For retailers and brands, striking a balance between personalisation and security is the ultimate challenge. The trust game It’s obvious that for brands and retailers, security and trust matter. Trust will need to be maintained throughout.

Kitaboo
MARCH 28, 2024
How DRM Protects eBook Content Encryption License Management Digital Watermarking Authentication Mechanisms IV. Digital Rights Management (DRM) is a sophisticated technology that helps retailers and publishers thwart unauthorized access and distribution of their eBooks. Implementing DRM in Digital Publishing V.

CIO Business Intelligence
MAY 28, 2022
Authentication problems are the most frustrating obstacles a customer will face online, and businesses must solve them if they want to increase their revenue and competitive edge. You might already have competitive prices, great customer service and a robust selection — but those hardly matter if customers get hung up on authentication.

CIO Business Intelligence
MAY 26, 2022
Authentication problems are the most frustrating obstacles a customer will face online, and businesses must solve them if they want to increase their revenue and competitive edge. You might already have competitive prices, great customer service and a robust selection — but those hardly matter if customers get hung up on authentication.

SecureWorld News
JANUARY 6, 2022
From these posts, the OAG compiled credentials to compromised accounts at 17 well-known online retailers, restaurant chains, and food delivery services. It is critically important that re-authentication be required for every method of payment that a business accepts. In all, the OAG collected credentials for more than 1.1

Kitaboo
OCTOBER 9, 2023
Authentic tasks encourage them to become involved in reflecting on their learning. After this, teachers provide authentic assessments for learners to evaluate their progress along the way. This brings more clarity to both students and their families about each learner’s academic and social progress.

SecureWorld News
NOVEMBER 22, 2023
Use multi-factor authentication ( MFA ) for any account that allows it. Sharing more than you feel comfortable with While you need to share data to make a purchase online, you should be wary of any retailer that is requesting more information than you feel comfortable sharing.

GeekWire
SEPTEMBER 29, 2020
Amazon One is set to debut Tuesday at two Amazon Go convenience stores near the company’s Seattle headquarters, giving customers an alternative to the regular process of checking into the automated retail stores, which normally involves using a QR code in an app. The Amazon One palm-scanning device. Amazon Photo).

CIO Business Intelligence
MAY 12, 2022
Providing a passwordless authentication experience leveraging WebAuthn and FIDO can solve both problems, giving organizations the win-win solution they need to remain competitive. IAM tools give organizations a way to authorize and authenticate users by relying on internal documentation validating identity. Authentication protections.

CIO Business Intelligence
OCTOBER 31, 2023
It pivots away from the “trust but verify” philosophy of the past and treats every entity as a new security perimeter that needs to mutually authenticate itself before gaining access to any resources. Zero-trust security principles can be a game changer for your security posture at the edge.

The Verge
NOVEMBER 5, 2021
Cryptocurrency and blockchain news presents many headlines that are hard to believe, so when a seemingly authentic press release ties a major retail outlet to second-tier crypto, it can take a moment to find out the truth. Photo Illustration by Thiago Prudencio/SOPA Images/LightRocket via Getty Images.

GeekWire
DECEMBER 18, 2020
We give consumers access to accurate, transparent, and bookable inventory that is available across our network of over 200 retailers and 75 cities. The pitch: “Fix Fake delivers risk-scoring software to automate authentication and find fakes for e-commerce marketplaces. We accelerate and reduce the cost to authenticate.

The Verge
SEPTEMBER 21, 2020
The aftermath of the graphics cards selling out in a matter of minutes at pretty much every major US retailer is that the limited supply that does still exist is being hawked on third-party seller sites in increasingly obnoxious fashions.

GeekWire
MARCH 21, 2021
Microsoft 365 authentication issue causes Microsoft Teams and other services to go down. Microsoft is investigating an authentication issue impacting multiple Microsoft 365 cloud services including Microsoft Teams, as well as Xbox Live. Cannabis retail tech startup Dutchie valued at $1.7B Most popular stories on GeekWire.

Network World
OCTOBER 19, 2016
About 40 percent of the patched flaws are located in Oracle E-Business Suite, Oracle Fusion Middleware, Oracle PeopleSoft, Oracle Retail Applications, Oracle JD Edwards, Oracle Supply Chain Products and Oracle Database Server. Many of these flaws can be exploited remotely without authentication to compromise the affected components.

CIO Business Intelligence
OCTOBER 20, 2022
Retailers are not the only people looking forward to the holiday season. Deploy email authentication standards on enterprise email servers to check and verify inbound emails. Some protocols like the Domain-based Message Authentication Reporting and Conformance (DMARC) help admins and users block unsolicited emails effectively.

CIO Business Intelligence
MAY 19, 2022
Customer demand for passwordless authentication has grown exponentially since smartphones first began offering built-in biometric readers. A staggering 93% of consumers preferred biometric authentication to passwords — and yet so many companies still force their customers to use risky, outdated login credentials. Your first clue?

Network World
JANUARY 18, 2017
Many of the flaws can be exploited remotely without authentication. The majority of the fixes are for flaws in business products such as Oracle E-Business Suite, Oracle Fusion Middleware, Oracle PeopleSoft, Oracle Retail Applications, Oracle JD Edwards, Oracle Supply Chain Products and Oracle Database Server.

CIO Business Intelligence
DECEMBER 19, 2023
5G also includes secure identity management, enhanced authentication and a core network architecture that can support network slicing, continuous secure connectivity for mobile devices and lower latency.

The Verge
SEPTEMBER 17, 2021
The publication described YKS as one of the platform’s largest Chinese retailers. Customers rely on the accuracy and authenticity of product reviews to make informed purchasing decisions and we have clear policies for both reviewers and selling partners that prohibit abuse of our community features.

CIO Business Intelligence
MARCH 24, 2023
Metaverse services can also help banks attract new customers. “We have a lineup of exciting projects, including creating a virtual bank for retail transactions and a non-fungible token marketplace using blockchain,” Singhal says. “We We need strong regulations like GDPR to define clear boundaries.

SecureWorld News
JULY 12, 2022
District of New Jersey, Onur Aksoy, a 38-year-old resident of Florida, was charged with running an operation to traffic fake Cisco equipment from China into the United States with an estimated retail value of more than $1 billion. Florida man makes millions of fake equipment.

The Verge
MAY 15, 2020
And especially during these times when demand is high for all kinds of tech, buying refurbished is sometimes the only way to get your hands on a product when retail channels are strained or just completely out of new merchandise. Refurbished products don’t usually get the spotlight from retailers like Best Buy, Amazon, or B&H Photo.

Network World
AUGUST 3, 2016
Many of the large payment card breaches that hit retail and hospitality businesses in recent years were the result of attackers infecting point-of-sale systems with memory-scraping malware. POS systems are specialized computers.

CIO Business Intelligence
NOVEMBER 20, 2023
Early in my career, I stayed in an authentic ryokan inn in Kyoto. The tool (MySH) now encompasses some brilliant features which gives us (Frucor Suntory Sales Team) the ability to have richer conversations with our retail partners,” saysScott McIver, Sales Field Manager at Frucor Suntory.
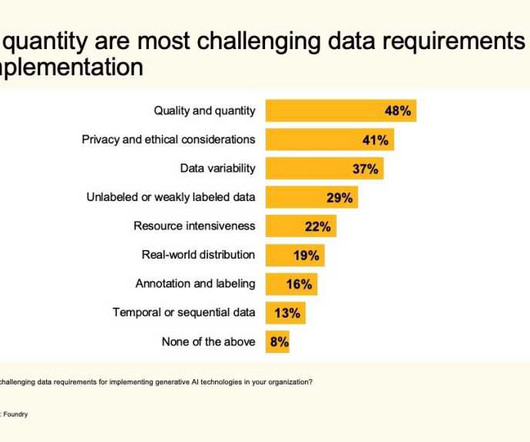
CIO Business Intelligence
OCTOBER 11, 2023
Security and privacy concerns Survey respondents have some ethical concerns about the use of generative AI, with security and privacy chief among them (both cited by 36%), followed by authenticity and trust (34%), intellectual property (31%), regulatory compliance (29%), bias (27%), and transparency (27%).

GeekWire
APRIL 1, 2021
WAX will provide verifiable authenticity for purchases of Funko NFTs. It currently operates physical retail locations at its Everett headquarters and in Hollywood, Calif. .” He said it’s important to to make Funko NFTs broadly accessible to fans by providing affordable entry pricing.

GeekWire
MARCH 5, 2021
If a film was going to capture the modern American landscape authentically, it’s hard to imagine doing so without including Amazon’s vast fulfillment operations as a supporting character. Amazon pays these associates $120 weekly to go toward their campground expenses.

GeekWire
DECEMBER 17, 2021
FlavorCloud’s software helps e-commerce retailers with international shipping. Stephen Benedict joined ID.me, a Virginia identity authentication platform, as chief product officer. . — Seattle startup FlavorCloud hired Mike Sanchez as chief revenue officer. ” Stephen Benedict.

CIO Business Intelligence
JUNE 5, 2023
Count them: the home Wi-Fi, the ISP, the Internet, a Domain Name System (DNS) provider, a content delivery network (CDN), applications distributed among multiple providers in multiple clouds, credit authentication companies, a private customer information database.

Kitaboo
MARCH 27, 2024
The need for unique access codes or authentication mechanisms allows DRM to ensure that only authorized users can view or download the content. Compliance with distribution agreements : Many distribution platforms and retailers require eBooks to be DRM-protected as part of their distribution agreements.

The Verge
DECEMBER 22, 2020
The story, “How Amazon Wins: By Steamrolling Rivals and Partners,” delves into Amazon’s various strategies for dealing with competitors and managing the Amazon Marketplace, its platform for third-party sellers that’s responsible for more than half of all its retail sales.

CTOvision
MARCH 17, 2015
Multi-factor authentication for both cloud-based accounts and on-premise Active Directory will now be part of Windows, rather needing a hardware solution to complete. Security has already been front and center early in 2015 with data breaches hitting some of the biggest names in the retail, financial and healthcare sectors.

The Verge
JULY 16, 2021
The giant retailer says it was concerned about how a new update to the Fakespot app was “wrapping” its website without permission, and how that could be theoretically exploited to steal Amazon customer data.

Galido
OCTOBER 7, 2019
According to sources by the end of 2020, online retail sales will the figure of 4,058 billion. Right from role-based authentication, PCI compliance, SSL security, Multi-level source validation, and the platform provides end-to-end security and covers every aspect of security. So, what to do? SEO friendly.

Dataconomy
AUGUST 29, 2023
Agriculture, retail, and transportation are just a few more examples of sectors benefiting from IoT integration. For example, retailers utilize AI to analyze consumer behavior, enhancing marketing strategies and product recommendations. Identify pain points, inefficiencies, and opportunities where IoT could make a significant impact.

Vox
NOVEMBER 16, 2023
So in an absence of authenticity and authority, where does an industrious internet user turn? On the results page, you’ll likely find a list of lists, some of which come from big-box retailers like Best Buy and others from professional review sites, including editorial sites like Wirecutter. Reddit, of course.

TM Forum
OCTOBER 19, 2021
Customers are less likely to visit retail shops to purchase phones or make changes to their plans, so fraudsters see an opportunity to impersonate them online. In addition to these changes, the Covid-19 pandemic has altered the behavior of both fraudsters and customers, making it difficult to distinguish between them.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content