Why Retailers Must Avoid Passwords
HID Global
APRIL 1, 2024
Discover how RFID reader technology revolutionizes retail with secure, passwordless authentication for enhanced efficiency and security. Learn more.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

HID Global
APRIL 1, 2024
Discover how RFID reader technology revolutionizes retail with secure, passwordless authentication for enhanced efficiency and security. Learn more.

Kitaboo
MARCH 28, 2024
These solutions help publishers and authors secure their content and protect eBooks from unauthorized distribution. How DRM Protects eBook Content Encryption License Management Digital Watermarking Authentication Mechanisms IV. Our secure cloud-based distribution ensures that your content is DRM-protected and encrypted.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CIO Business Intelligence
JULY 10, 2023
It can often feel as though trust and authenticity are in short supply these days. This has reinforced concerns around data privacy and security. In the midst of message and content overload, consumers demand personal, in the moment, experiences that feel safe and secure.

CIO Business Intelligence
MAY 2, 2022
Password-based authentication is likely the most widely used method of authenticating users to online services. Password-based authentication is used because it is easy to understand and implement. However, this comes at the cost of weak security and a poor user experience. Password-based authentication isn’t working.

CIO Business Intelligence
DECEMBER 19, 2023
When making decisions about network access, businesses need to be aware of and assess the security implications associated with network technology to help keep their digital assets protected. Cyber hygiene best practices include device security , cyber security education , and secure networking strategies.

CIO Business Intelligence
OCTOBER 16, 2023
But casino gaming companies MGM Resorts International and Caesars Entertainment were caught short in this area in recent weeks by hackers using identity-based and social engineering attacks that spoofed identity to gain access to secure systems. IBM Security pegged that same number higher, to 95%.

SecureWorld News
AUGUST 25, 2023
Common Labor Day scams to watch out for Fake Retail Promotions: Cybercriminals create counterfeit websites or email campaigns that mimic legitimate retailers offering massive discounts on popular products. Email Filters and Authentication: Implement robust email filters that can identify and quarantine phishing emails.

CIO Business Intelligence
MAY 12, 2022
Simultaneously, a Norton report showed that consumers expressed concerns over data privacy and security, with 58% of adults saying that they are more worried than ever about being a victim of cybercrime [2]. IAM tools give organizations a way to authorize and authenticate users by relying on internal documentation validating identity.

CTOvision
MARCH 17, 2015
Last year, Enterprise IT was dramatically shaped by the influx of security breaches, data leaks and a new wave of hackers. This year, two of 2014’s biggest stories will intersect as security and Windows 10 prepare to re-shape the Enterprise. Security Spending. Windows 10. and is finally giving Enterprises exactly what they need.

ComputerWorld IT Management
JUNE 20, 2016
Retailers have this love-hate relationship with EMV, in that they love to hate EMV. With that in mind, it's easy to understand why major retailers — Walmart last month and Home Depot last week — are suing Visa and MasterCard in an attempt to fight chip cards any way they can. Of course, the retail argument isn't quite phrased that way.

CIO Business Intelligence
OCTOBER 31, 2023
Unfortunately, as you extend computing out to the edge, your organization becomes increasingly vulnerable to security risks. As you can see, security breaches at this level can have a devastating impact on people and your business. Zero-trust security principles can be a game changer for your security posture at the edge.

CIO Business Intelligence
MAY 28, 2022
Though customers are concerned about privacy and security , they are unwilling to sacrifice a seamless journey for unseen benefits. Authentication problems are the most frustrating obstacles a customer will face online, and businesses must solve them if they want to increase their revenue and competitive edge.

CIO Business Intelligence
MAY 26, 2022
Though customers are concerned about privacy and security , they are unwilling to sacrifice a seamless journey for unseen benefits. Authentication problems are the most frustrating obstacles a customer will face online, and businesses must solve them if they want to increase their revenue and competitive edge.

CIO Business Intelligence
OCTOBER 20, 2022
Retailers are not the only people looking forward to the holiday season. In fact, CIO has reported that it takes only a few minutes for experienced hackers to set up a social engineering attack against enterprises (and their managed service providers) that consider themselves to be secure and protected.

Kitaboo
MARCH 27, 2024
By securing patents, copyrights, trademarks, etc., Understanding ePub DRM Let’s talk about ePub DRM — an important option when it comes to securing your precious creations. Understanding ePub DRM Let’s talk about ePub DRM — an important option when it comes to securing your precious creations.

GeekWire
SEPTEMBER 29, 2020
Even so, Amazon’s use of biometrics in stores and other commercial settings promises to attract scrutiny at a time of heightened awareness of digital security and privacy, testing the limits of customer trust in the company. But Amazon’s growing retail footprint could take adoption of biometrics to a new level. .

SecureWorld News
NOVEMBER 22, 2023
Use multi-factor authentication ( MFA ) for any account that allows it. However, public Wi-Fi is not very secure; you shouldn't ever online shop or access important accounts (like banking) while connected to public Wi-Fi. Turn on automatic software updates , or install updates as soon as they are available.

CIO Business Intelligence
MARCH 24, 2023
We have a lineup of exciting projects, including creating a virtual bank for retail transactions and a non-fungible token marketplace using blockchain,” Singhal says. “We In addition to creating ground-breaking experiences, the metaverse, like other emerging technologies, brings a new set of security challenges.

Kitaboo
OCTOBER 9, 2023
Authentic tasks encourage them to become involved in reflecting on their learning. After this, teachers provide authentic assessments for learners to evaluate their progress along the way. This brings more clarity to both students and their families about each learner’s academic and social progress.

SecureWorld News
JANUARY 6, 2022
From these posts, the OAG compiled credentials to compromised accounts at 17 well-known online retailers, restaurant chains, and food delivery services. It is critically important that re-authentication be required for every method of payment that a business accepts. In all, the OAG collected credentials for more than 1.1

CIO Business Intelligence
JUNE 5, 2023
Count them: the home Wi-Fi, the ISP, the Internet, a Domain Name System (DNS) provider, a content delivery network (CDN), applications distributed among multiple providers in multiple clouds, credit authentication companies, a private customer information database. Problems often take a long time to identify and resolve.
CIO Business Intelligence
OCTOBER 11, 2023
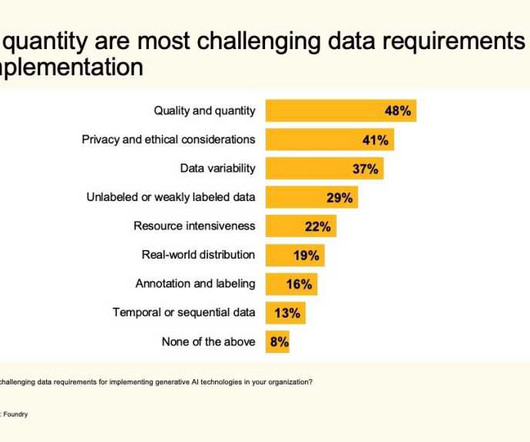
Security and privacy concerns Survey respondents have some ethical concerns about the use of generative AI, with security and privacy chief among them (both cited by 36%), followed by authenticity and trust (34%), intellectual property (31%), regulatory compliance (29%), bias (27%), and transparency (27%).

CIO Business Intelligence
DECEMBER 21, 2023
The diversification of payment methods and gradual increase in the volume of online transactions have cast a spotlight on the need for payment security compliance within the airline industry. With the new, recently onboarded Payment Card Industry Data Security Standard (PCI DSS) v4.0, she wonders. Well not exactly. The PCI DSS v4.0,

Network World
OCTOBER 19, 2016
About 40 percent of the patched flaws are located in Oracle E-Business Suite, Oracle Fusion Middleware, Oracle PeopleSoft, Oracle Retail Applications, Oracle JD Edwards, Oracle Supply Chain Products and Oracle Database Server. Many of these flaws can be exploited remotely without authentication to compromise the affected components.

Network World
JANUARY 18, 2017
Oracle released its first batch of security patches this year, fixing 270 vulnerabilities, mostly in business-critical applications. Many of the flaws can be exploited remotely without authentication.

Galido
OCTOBER 7, 2019
According to sources by the end of 2020, online retail sales will the figure of 4,058 billion. Right from managing data security to generating traffic, retaining customers, product return, and refund procedures, and the list goes on. Lastly, it also releases security patches and detailed vulnerability reports on a regular basis.

CIO Business Intelligence
MAY 19, 2022
Customer demand for passwordless authentication has grown exponentially since smartphones first began offering built-in biometric readers. A staggering 93% of consumers preferred biometric authentication to passwords — and yet so many companies still force their customers to use risky, outdated login credentials. Your first clue?

The Verge
JULY 16, 2021
The giant retailer says it was concerned about how a new update to the Fakespot app was “wrapping” its website without permission, and how that could be theoretically exploited to steal Amazon customer data. We have more amazing products coming soon that will make secure shopping the gold standard for eCommerce.

Dataconomy
AUGUST 29, 2023
Agriculture, retail, and transportation are just a few more examples of sectors benefiting from IoT integration. Smart cities will continue to evolve, leveraging IoT to enhance sustainability, security, and quality of life. As IoT devices proliferate, ensuring robust encryption, authentication, and regular updates will be crucial.

CIO Business Intelligence
NOVEMBER 20, 2023
Early in my career, I stayed in an authentic ryokan inn in Kyoto. SAP BTP then provided the foundational capabilities including security, mobile platform, and integration to bring the new sales journey to life.” After work, my colleague and I discovered the local dishes and Suntory scotch—a first.

CIO Business Intelligence
JULY 11, 2022
Retailers continue to adopt a digital-first approach to customer experience, both in-store and online. To meet the customer demands of a digital-first business model, retailers need to address their critical digital infrastructure and rethink network design and cybersecurity. Retail-specific vulnerabilities.

GeekWire
JANUARY 12, 2021
Identity authentication startup Auth0, which raised a $120 million Series F round in July, added three new board members: • Former Hewlett Packard Enterprise Chief Sales and Marketing Officer Sue Barsamian. The 9-year old company provides security technology and analysts, with a focus on healthcare, financial and government organizations.

TM Forum
OCTOBER 19, 2021
This is a very concerning trend and telcos are much preoccupied by the security of their customers. Customers are less likely to visit retail shops to purchase phones or make changes to their plans, so fraudsters see an opportunity to impersonate them online. Empowering business assurance with artificial intelligence.

The Accidental Successful CIO
FEBRUARY 17, 2021
What should you be doing as CIO to keep your people and your company secure? Should mobile phone users be concerned about relying on their mobile phones for text messaging based two-factor authentication? The good news is that what is happening is that a layered approach to security is being adopted.
The Verge
SEPTEMBER 1, 2021
Password managers like 1Password are a great way to store your login credentials and beef up your security, however, one that can also save you plenty of time. Amazon’s current deal comes just a week after the retailer also cut the price of the 55-inch model by $200 , bringing it to a record low of $1,098.

The Verge
JANUARY 27, 2022
Shifting away from cameras to TVs, several retailers are once again selling TVs at prices we last saw during Black Friday and Cyber Monday in the run-up to Super Bowl Sunday. They normally retail for $149.99, but today, Woot is selling them in a variety of colors, including graphite, white, olive, and lavender, for $99.99.

CIO Business Intelligence
JULY 31, 2023
Foundry’s gen AI survey found that retail CIOs are leading the way on identifying use cases (49%), followed by IT leaders in the manufacturing (42%), technology (42%), and financial services (32%) sectors. Buyers agreed most strongly with the sentiment that generative AI will enable their employees to focus on higher-value tasks.

CIO Business Intelligence
FEBRUARY 7, 2023
Leonie, an agile delivery manager working in the retail industry, who only gave her first name, saw this first-hand earlier in her career. Cybsafe Some organizations are tailoring their social policies to be more inclusive, such as at security awareness training firm Cybsafe. We need strong allies, but it has to be authentic.

CIO Business Intelligence
MARCH 9, 2022
It’s important to note that even though your devices may not utilize 3G for content transmission, they may use it to authenticate with the carrier network or simply have a radio that speaks to 3G network, both pose a possible bad outcome for your devices. Phasing out POTS. 2 deadline.

The Verge
OCTOBER 1, 2020
Palm recognition is thought to be more secure than other biometric methods. From a security point of view, palm scanning has some key advantages over other biometrics. There’s definitely something to say for the advanced security [of palm scanning].”. The scanners can then identify someone “in seconds” without skin contact. (A

CIO Business Intelligence
NOVEMBER 28, 2023
And while all organizations work hard to prevent attacks through traditional security measures such as multi-factor authentication, patching, training, and more, the bad guys increasingly find their way in through poorly thought-out, scattered access and identity management practices.

Cloud Musings
APRIL 25, 2013
Next week I will be participating in the inaugural session of What’s Next in IT Debate Series , a new program of authentic debates and conversations on key technology topics. Cloudcuity Secure, Unified Cloud Management and Control Services. Jackson 2012 ). at 3:30 AM. Email This BlogThis! Share to Twitter Share to Facebook.

The Accidental Successful CIO
JULY 8, 2020
CIOs need to figure out how robots can get a new retail job Image Credit: Photo by Rock’n Roll Monkey on Unsplash. One way that the person with the CIO job is trying to help out is by taking the robots that have become an indispensable part of almost every warehouse and move them into retail settings. Say Hello To Retail Robots.

Dataconomy
MAY 30, 2023
Ambient intelligence in commerce Retailers have long employed wireless technologies like iBeacon to engage with smartphone users within brick-and-mortar stores. Examples of ambient intelligence Amazon Go: Amazon Go is a project by the e-commerce giant Amazon that showcases the implementation of ambient intelligence in the retail sector.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content